
By nature, data and communications surrounding products manufactured for use in defense applications must involve some level of heightened security. But what exactly does this look like, and what measures are necessary? In January 2020, the United States government’s National Institute of Standards and Technology (NIST, Gaithersburg, Md., U.S.) introduced the second revision of NIST 800-171, a document outlining cybersecurity requirements for protecting the confidentiality of controlled unclassified information (CUI) — information considered sensitive but not entirely classified — held by organizations and companies outside of the federal government. Important for the composites industry, the new standards affect companies working under contract with the U.S. Department of Defense (DOD), as well as suppliers to those companies.
NIST 800-171 Revision 2, which supersedes the Revision 1 document released in 2018, was released for a preliminary comment period between January and March 2020, partially phased in this spring and is scheduled for widespread rollout this fall. According to Michael Flavin, director of IT sales and marketing at consultancy firm Saalex Information Technology (SaalexIT, Camarillo and Temecula, Calif., U.S.), there may be as many as 300,000 companies, including composites fabricators or suppliers, within the scope of NIST 800-171 by 2025.
Goals of the new protocol, according to Flavin, include:
- Enforcement of better “cybersecurity hygiene” — or cybersecurity best practices;
- protection of sensitive data from foreign hackers; and
- protection of intellectual property considered vital to national security.
In addition, the new protocol does not just require stricter cyber monitoring, but also documentation of that monitoring.
NIST 800-171 categorizes its recommendations into 14 families: access control, awareness and training, audit and accountability, configuration management, identification and authentication, incident response, maintenance, media protection, personnel security, physical protection, risk assessment, security assessment, system and communication protection and system and information integrity.
Common cybersecurity issues include inadequate firewalls, poor password use and inadequate training.
However, according to Flavin, not all companies are required to comply to the same level of cybersecurity. Requirements are divided among five levels, arranged in descending order according to the sensitivity of the information involved, with Level 1 indicating the most sensitive information requiring the most stringent cybersecurity measures, says Flavin. Moreover, the compliance level is based on the DOD contract and affects all companies associated with that contract — in other words, both the company with the direct contract and all relevant suppliers for that project are required to comply to the same level of cybersecurity.
A failure to comply, Flavin adds, could lock a supplier out of future contracts, so the protocol will likely result in “weeding out” of suppliers with weak cybersecurity practices.
Most common cybersecurity issues
“The last thing you want is to find out from the FBI that you’ve been breached. Which has happened,” says Flavin.
According to Flavin, large companies tend to have sophisticated IT systems that can meet the requirements of NIST 800-171, but smaller firms may not have this in place. The vulnerability presented by smaller companies shouldn’t be underestimated, he adds: “Everyone thinks big companies, like Bank of America, are the target, but if an intruder can break into several small, weak targets, they will do it, and it can be just as destructive.”
Common cybersecurity issues that companies have, says Flavin, include inadequate firewalls, poor password use and inadequate training that puts employees at risk for phishing scams or ransomware. In addition, Flavin says, many company IT systems use connected network systems that should be segregated, to separate data into segmented networks, with sensitive information only accessible by certain users.
Becoming NIST 800-171 compliant
What can a company do to assess whether it is in compliance with NIST 800-171, and to make any needed adjustments?
Compliance with NIST 800-171 will require some planning for many companies, says Flavin. For example, compliance could cost a company $500-$2,000 per employee per year, depending on the level of security needed. On top of that, an annual cybersecurity audit may be necessary.
The first step is to consider both the kind of work that your company currently does as well as what kind of work you might do in the future that could have potentially more sensitivity concerns involved with it. “It’s better to raise the bar on cybersecurity proactively, and not try to catch up after the fact,” says Flavin .
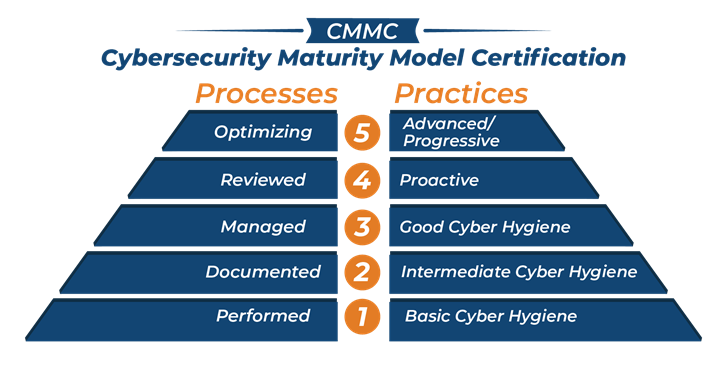
Source | SaalexIT
The next step, he says, is to get a third-party assessment of data security from a company like SaalexIT. If you are unsure what the data security requirement level is, he recommends targeting Level 3 compliance as a baseline. Flavin adds that looking to third-party assessment companies — many of which perform assessments remotely given current pandemic-related travel restrictions — should not be seen as a sign that a company does not trust the measures put in place by its in-house IT team: “The goal is not to denigrate current IT staff, but to understand and fix vulnerabilities. This requires cooperation of IT.”
SaalexIT helps companies by performing a “gap assessment” to illuminate potential problem areas and suggest a course of action toward certification. “We look at the type of work being done and the access to classified information under the contract and the level required. We then make recommendations to the customer about their data weaknesses and what must be done to come into compliance with the level,” says Flavin. This gap assessment looks at policies and procedures, employee data security training and data authentication procedures such as logins and passwords. For example, says Flavin, companies need to consider whether employees are accessing files outside their area of work or responsibility. Ultimately, SaalexIT is then able to present a project plan with milestones for better site security, a roadmap for compliance and related costs.
Finally, Flavin says that to fully comply with NIST 800-171, companies can be certified by a third-party certification assessor organization (C3PAO) appointed by the DOD. The system is still in the planning and organization stages, but certification will adhere to the Cybersecurity Maturity Model Certification (CMMC, see image above) outlined by the DOD.
Before the requirements go into full effect, Flavin recommends that affected companies start now and seek out cybersecurity experts for third-party assessment. “Mindset should be when, not if, you will be attacked,” he says. “And you must mitigate that risk.”
Related Content
From the CW Archives: Airbus A400M cargo door
The inaugural CW From the Archives revisits Sara Black’s 2007 story on out-of-autoclave infusion used to fabricate the massive composite upper cargo door for the Airbus A400M military airlifter.
Read MoreLarge-format 3D printing enables toolless, rapid production for AUVs
Dive Technologies started by 3D printing prototypes of its composite autonomous underwater vehicles, but AM became the solution for customizable, toolless production.
Read MoreNorthrop Grumman, U.S. Air Force introduce B-21 Raider
The sixth-generation, composites-intensive strategic bomber aircraft represents new capabilities and flexibility supported by an advanced digital ecosystem.
Read MoreIndustrializing additive manufacturing in the defense/aerospace sector
GA-ASI demonstrates a path forward for the use of additive technologies for composite tooling, flight-qualified parts.
Read MoreRead Next
VIDEO: High-rate composites production for aerospace
Westlake Epoxy’s process on display at CAMX 2024 reduces cycle time from hours to just 15 minutes.
Read MorePlant tour: A&P, Cincinnati, OH
A&P has made a name for itself as a braider, but the depth and breadth of its technical aptitude comes into sharp focus with a peek behind usually closed doors.
Read MoreCFRP planing head: 50% less mass, 1.5 times faster rotation
Novel, modular design minimizes weight for high-precision cutting tools with faster production speeds.
Read More

.jpg;width=70;height=70;mode=crop)













.jpg;maxWidth=300;quality=90)







